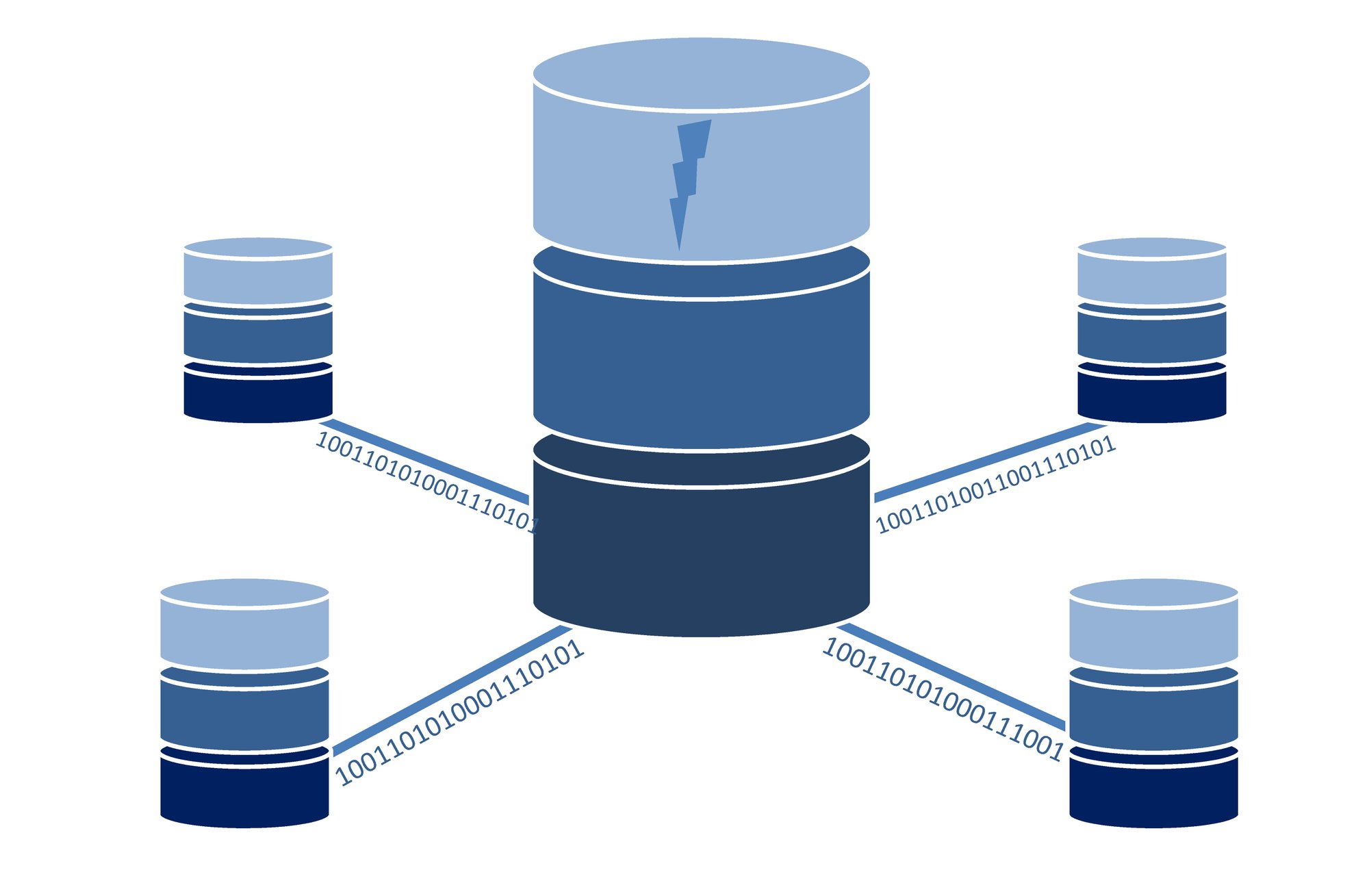
Building a DR that you can count on is a challenge for anything deployed in the cloud. DR is an important characteristic of any cloud deployment. While it is possible that an entire region can go down, having a...
What is Server Hardening? Providing several means of protection to the computer is known as Server hardening. Hardening provides layers of security at the host level, application level, operating system level, physical level, user level, and all the sublevels....
The news of the cyber-attack on Cosmos Bank servers, resulting in syphoning of Rs. 94 crore to foreign bank accounts broke open on August 14, 2018. Within minutes, this turned out to be a major headline for the day...
You must have come across situations where your AWS account is misused. This 17-point checklist makes sure your AWS account is not misused. AWS Security starts with protecting your AWS Account. Overlooking the account security can lead to a...
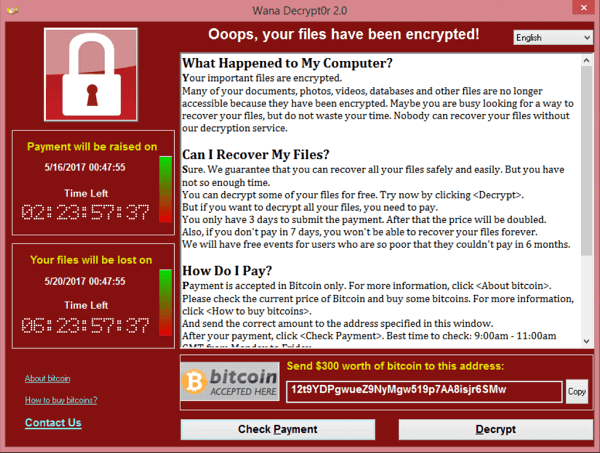
Ransomware has been playing havoc every few months. Most of the Users who have fallen victim to it, have either lost their years of data or have paid ransom in Bitcoin to get their data back, in the absence...
Almost all modern computers are at risk today, thanks to an architectural flaw in the way processors allow access to memory. Meltdown and Spectre CPU vulnerabilities affect all processors from Intel, ARM, and AMD. The year 2018 started with...
Are you concerned with your monthly bill going way over your AWS pricing estimate? Do you feel your cloud infrastructure costs are spiralling out of control? Here are a few common issues that can lead to an inflated bill....
Is your organization constantly battling to secure Email and still falling prey to Cyber espionage? Perhaps, this article may ring a bell on your concerns.