
What is Server Hardening?
Providing several means of protection to the computer is known as Server hardening. Hardening provides layers of security at the host level, application level, operating system level, physical level, user level, and all the sublevels. Server hardening is also known as system hardening.
Secure your OS by Server Hardening
Just as your website, web applications or any online business is secured, it is important to harden the OS. Even though you are spending money on WAF or on security plugins, without OS hardening can be extremely vulnerable to hackers.
Most of the web is migrating to the cloud, as you get higher control in the cloud but requires some system admin skills to manage the VM. Below is the list of security tips to secure Ubuntu and CentOS VM in the cloud:
Change SSH Default Port
By default, SSH daemon listen on port 22 which means if anyone figures out your IP address, an attempt to connect to your server. You may avoid this using strong password, but still, they can launch brute force attacks and disturb the servers. The possible solution to this is changing the SSH port so that even if someone knows the IP address, they cant attempt to connect using the default SS port.
To change the SSH port in Ubuntu/CentOS follow the below steps:
- Login to VM with root privilege
- Take back up of sshd_config
- Use the VI editor to open the file :
vi /etc/ssh/sshd_config - In the beginning of the file look for the line which has Port 22 :
# What ports, IPs and protocols we listen for Port 22 - Change the port number to 5000 or any other unused port number
- Save the file and restart the SSH daemon :
service sshd restart
Since we’ve changed the default port, no one can try to connect to your server, but you should remember to connect using the new port number 5000. Also, you can change the port number in the SSH client or terminal as below assuming your server IP is A.B.C.D :
ssh -p 5000 username@A.B.C.D
Protection from Brute Force Attacks
Initiating the brute force is the common method used by a hacker to take control of your web applications such as WordPress, Joomla etc. You can use one of the two programs to harden your Linux system from brute force that is SSHGuard and Fail2Ban.
SSHGuard continuously monitors the service from the system and blocks recurring unsuccessful attempts. You can install the SSHGuard by following the below methods.
Ubuntu
apt-get install SSHGuard
CentOS
wget
ftp://ftp.pbone.net/mirror/ftp5.gwdg.de/pub/opensuse/repositories/home:/hornos:/centos/CentOS_CentOS-6/x86_64/sshguard-1.5-7.1.x86_64.rpm
rpm -ivh sshguard-1.5-7.1.x86_64.rpm
Fail2Ban is another alternative program to protect your SSH port. They automatically update the iptables rule if it detects any unsuccessful login attempts after reaching a certain threshold. Install Fail2Ban using the below commands :
Ubuntu
apt-get install fail2ban
Centos
yum install epel-release yum install fail2ban
Disabling Password Based Authentication
If you’ve many users who often log in from public computers, it might be cumbersome to exchange the key every time. We recommend disabling password-based authentication to avoid this condition. Assuming you have already set up the SSH key exchange you can disable the password authentication as follows:
- Using VI editor modify the file /etc/ssh/sshd_config
- Add the below line :
PasswordAuthentication no - Reload SSH Daemon
Protection from DDoS Attacks
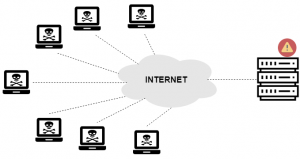
DDoS attacks can occur at any security level and one should be prepared to avoid this. To prevent from DDoS attacks you should hide your Origin IP of your cloud server.
- Use the load balancers by configuring it to internet-facing, such that server IP is not exposed to the internet.
- Use CDN to improve the performance and the security of the server. By using the CDN, you are exposing the IP address of the CDN provider and your Origin IP remains unexposed.
- Leverage the IPTables to block suspicious requests, bogus TCP flag, private subnet etc.
- Use either hardware-based firewall or software-based firewall.
Take Regular Backup
Taking regular back saves you when the breach occurs. All the cloud providers offer the daily backup feature. If you are using AWS, Azure or Google Cloud then make sure to enable daily snapshot. Using backup, you can restore the entire VM and you will be back in business with a small downtime.
Update the OS Regularly
OS should be regally updated whenever the new update is released to make sure the servers are not exposed to the latest security vulnerabilities.
Keep the Ports Closed
To run a website in Virtual Machine, you need to only keep the ports 80 (HTTP) or 442 (HTTPS) open. AWS cloud offers security group which allows you to open the required ports. And for the more refined control you can use the network ACL. Similarly, Google Cloud offers Firewall rules to make the necessary changes to ports.
About InterPole
InterPole was established in 1996 and has been engaged in web hosting, email, and management of IT infrastructure. InterPole pioneered with Virtual Private Servers in 2004 and Cloud Hosting in 2008. Over the years, InterPole has worked with over 6200 mid-sized businesses and startups, and have assisted them in their journey towards the adoption of modern technologies through the Internet. InterPole is a Standard Consulting Partner of Amazon AWS and Microsoft Azure. With this partnership, provides Managed AWS service and maintains a team of engineers who are trained and certified for the specific cloud platforms. These benefits companies in defining their cloud strategy and making a well-planned journey, reliably and cost-effectively.

